SASE. What is it?
In this post I’ll explain what it is, what it does!
Want to configure it yourself? That will come in Part 2.
So, what is SASE? Secure Access Service Edge. Now you know exactly what it is right? No? I had the same thought when I first started looking into it.
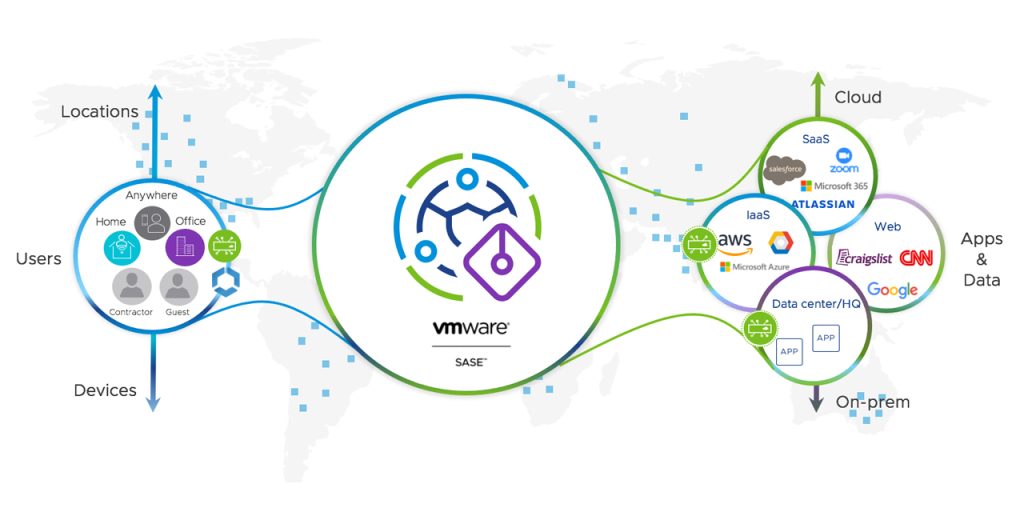
It basically means you can connect to a Server/PoP (Point of Presence), that can check your internet traffic and make cool decisions based on the content. Here is a picture of how the flow looks from left to right:
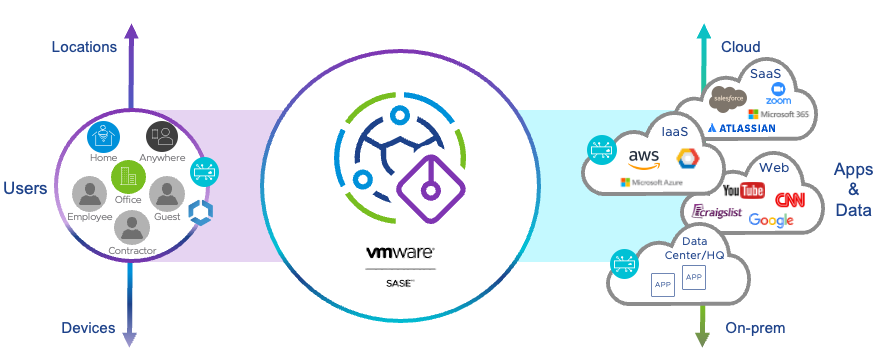
You, the user, connects to a VMware SASE PoP. From there it could connect you to the cloud, websites and internal resources. VMware SASE then decides whether this is allowed or not, based on rules created within SASE.
Still no clue what it means? Let me explain with an example:
You get an email with a malicious link in it, you click on it and it’s magically blocked. How? Because VMware SASE saw that it was a malicious link and blocked it before it could affect your device. Great right?
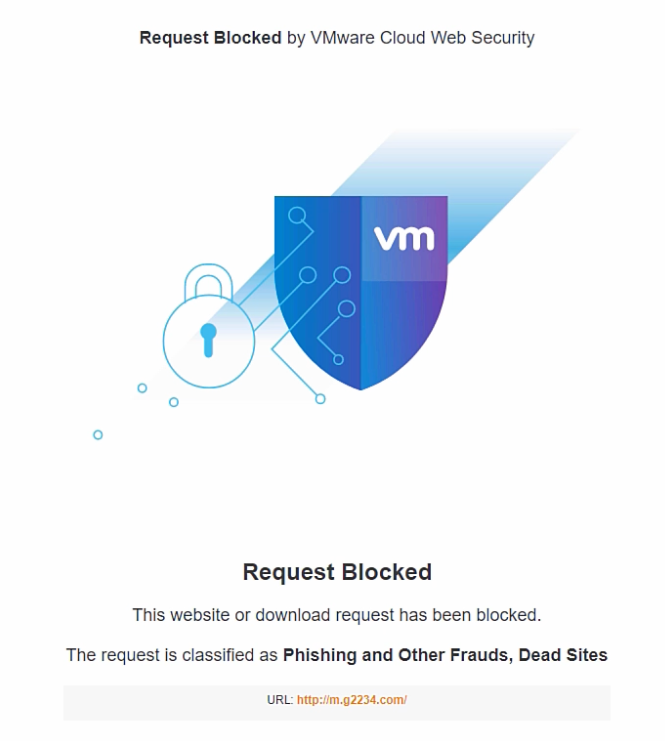
The cool thing with VMware SASE is that it can block or check the things you do online, without interfering with user experience. It can even improve user experience, as it integrates with Velocloud SD-WAN. This all means, as a company, you can make sure you keep your digital estate safe. And users can browse while being safe (or safer at least).
Through VMware SASE, multiple services are offered:
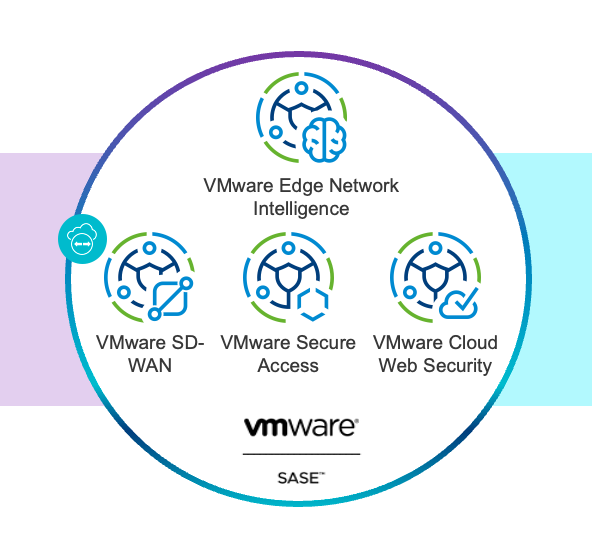
- Secure Access is a Zero Trust Network Access (ZTNA) platform that provides encrypted tunneled access between any entity and internal applications (DC, IaaS or PaaS).
- Cloud Web Security is a Secure Web Gateway (SWG) platform based on proxy architecture that provides security services for Internet or SaaS traffic.
- SD-WAN is a software-defined overlay network virtualisation technology for transporting WAN communications that ensures the best possible performance and security.
The great benefit that VMware offers, is a tightly integrated and efficient platform with one management plane for both the Security and Networking sides of SASE. And you can also start with just the networking or security functionality and add more over time.
Within Cloud Web Security, several protections are offered:
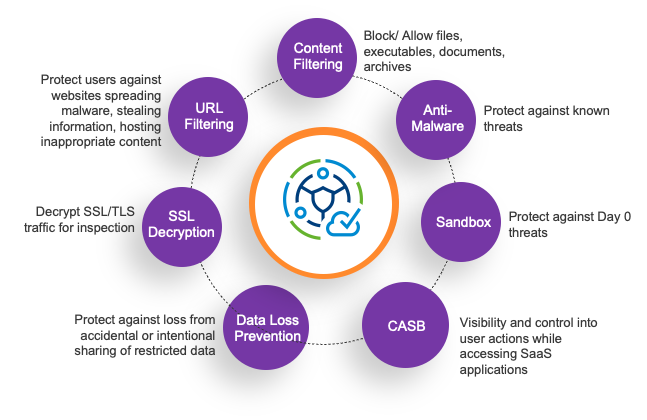
- SSL decryption: 80% of web applications are SSL encrypted. By decrypting the traffic, CWS can see what data is inside the traffic so it can make decisions. It’s also possible to bypass SSL decryption when needed, such as specific websites.
- URL filtering helps IT control which websites users can access based on categories or threats.
- Content Filtering helps control the type of document and file that can be uploaded or downloaded.
- Anti- Malware helps protect users when they download emails, documents or access active web sites against known viruses.
- Sandbox. New viruses continue to get introduced daily and it is imperative the solution can respond to Day-0 malware attacks. CWS uses a Sandbox to offer protection from those Day-0 attacks by unpacking in a sandbox.
- Cloud Access Security Broker enables IT teams to get visibility into sanctioned and unsanctioned SaaS applications. This helps IT determine what activities can users undertake when they access these applications. Can employees login, upload and download files from Drop Box? Should summer interns only be allowed to upload documents to Drop Box? Can contractors who are allowed to download files from Drop Box attach that file to the LinkedIn email? CASB helps with this.
- Data Loss Prevention. CWS ensures sensitive company data does not leave the enterprise perimeter, such as phone numbers or bank details. This is possible for both HTTP as HTTPS data, and for files that contains the data.
With all these features, you can keep your data and users safe. Integrating it with UEM, it can be easily deployed too.
That explains the what, the how comes in Part 2!
Questions? Let me know in the comments.

Tesfaye Assefa says:
Interesting
7 July 2022 — 7:59 am